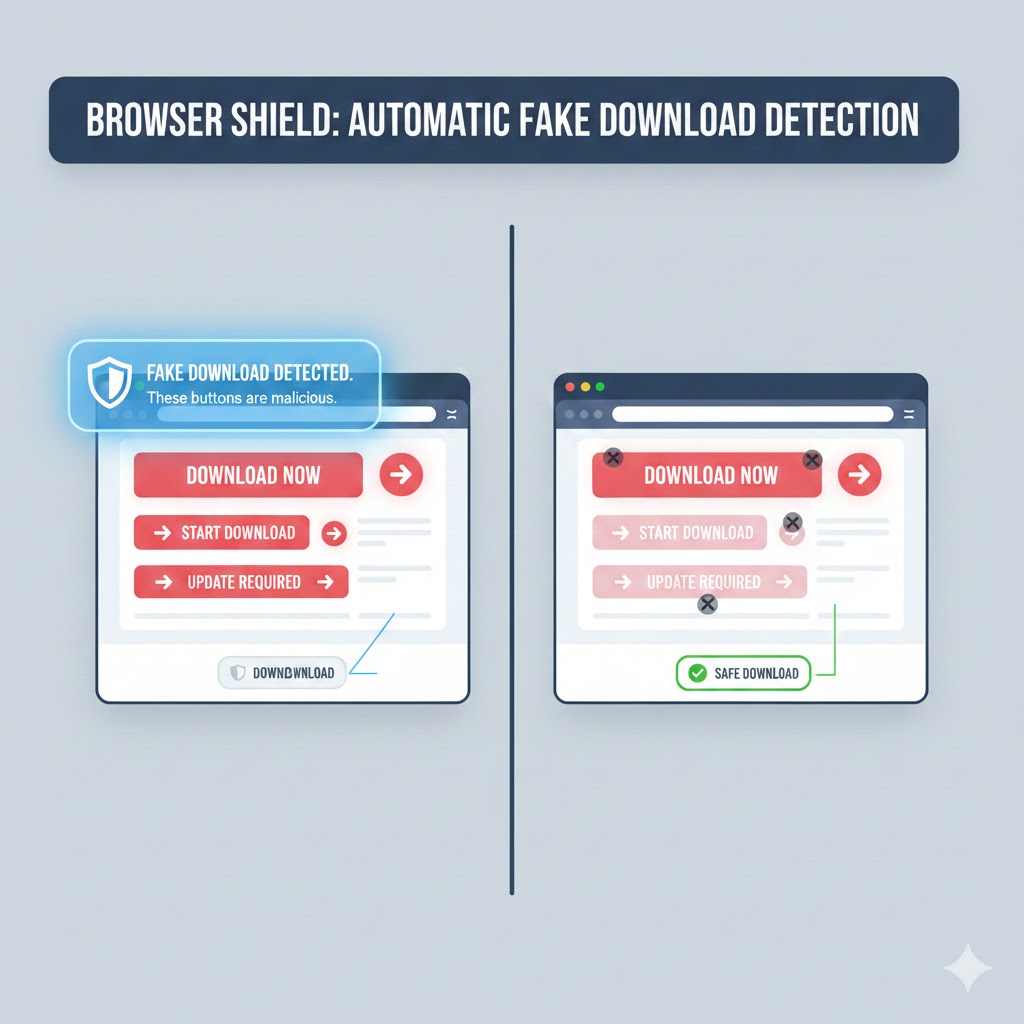
Have you ever visited a website to download legitimate software, only to find yourself surrounded by multiple download buttons—each one looking more official than the last? You click what appears to be the real download button, and suddenly your computer begins downloading unwanted software, adware, or worse. The frustration of navigating through deceptive download buttons has plagued internet users for years, but modern browsers now include powerful features that can Browser Feature detects fake download buttons and protect you from these malicious traps.
This comprehensive guide explores the cutting-edge browser technologies that automatically identify and warn you about fake download buttons, helping you avoid malware, unwanted toolbars, and deceptive advertising. Understanding these protective features and knowing how to enable them can save you from countless security threats and frustrating cleanup operations.
The landscape of online deception has evolved significantly, with scammers becoming increasingly sophisticated in their attempts to trick users. However, browser developers have responded with equally advanced protection mechanisms designed to Browser Feature detects fake download buttons before you fall victim to their schemes. Let’s explore these powerful security features and learn how to browse the internet with confidence.
1. Understanding the Fake Download Button Problem
Before diving into browser protections that detect fake download buttons, it’s essential to understand the scope and nature of this pervasive online threat.
The Anatomy of Deceptive Download Pages
Legitimate download pages have been infiltrated by advertising networks that intentionally create confusion. When you visit a site to download free software, you might encounter five or more prominent buttons labeled “Download,” “Download Now,” or “Get It Free.” Only one of these buttons actually initiates the legitimate download you’re seeking.
The fake buttons are carefully designed to mimic the appearance of legitimate download controls. They use similar colors, fonts, and positioning to the real button, making it nearly impossible for average users to distinguish between authentic and malicious options. These deceptive elements are strategically placed in positions where users naturally look first, such as the top-right corner or center of the page.
Advertisers and malicious actors pay website owners significant money to host these fake download buttons. For struggling websites that offer free downloads, this advertising revenue can be substantial, creating a financial incentive to allow deceptive practices despite the harm to users.
Common Tactics Used by Fake Download Buttons
Fake download buttons employ various psychological and visual tricks to deceive users. They often use urgency language like “Download Now—Limited Time” or “Fast Download” to pressure quick clicking without careful evaluation. File size indicators, timer countdowns, and supposed “download statistics” add false legitimacy.
Many fake buttons incorporate visual elements that suggest official software branding, operating system compatibility icons, or security badges. These trust signals make users believe they’re clicking the legitimate download option when they’re actually triggering unwanted downloads or redirects.
The most sophisticated fake download buttons use JavaScript to detect mouse movement and dynamically adjust their position or appearance to capture clicks. Some even present themselves as download progress indicators or security scans that require user interaction to “complete” the download.
The Real Consequences of Clicking Fake Buttons
Clicking a fake download button can trigger various harmful outcomes. The most common result is downloading bundled software packages containing adware, browser hijackers, and potentially unwanted programs. These applications modify your browser settings, inject advertisements into web pages, and collect browsing data without proper consent.
More serious consequences include downloading actual malware such as trojans, spyware, or ransomware. Some fake download buttons redirect users to phishing pages designed to steal credentials or financial information. Others subscribe users to premium SMS services or unwanted subscription services.
Even when fake buttons don’t directly install malware, they waste time and bandwidth downloading useless files. Users then face the tedious process of uninstalling unwanted software, cleaning browser settings, and running security scans to ensure system integrity.
2. Google Safe Browsing Technology
One of the most powerful systems designed to detect fake download buttons is Google Safe Browsing, a technology integrated into multiple browsers and used by billions of users worldwide.
How Safe Browsing Works Behind the Scenes
Google Safe Browsing maintains massive databases of known malicious websites, phishing pages, and deceptive download sources. These databases are continuously updated as Google’s automated systems crawl the web, analyzing billions of pages daily for suspicious patterns and reported threats.
When you attempt to visit a website or click a download link, your browser checks the URL against Safe Browsing’s database. This verification happens in milliseconds, creating no noticeable delay in your browsing experience. If the URL matches a known threat, your browser displays a warning page before allowing you to proceed.
The system uses machine learning algorithms trained on millions of malicious pages to identify characteristics common to deceptive download pages. These algorithms analyze page structure, button placement, advertising networks, and historical complaint patterns to calculate threat scores for websites and specific page elements.
Real-Time Protection and Warning Systems
Google Safe Browsing doesn’t just block known threats—it provides real-time protection by analyzing new and updated pages as you encounter them. When you navigate to a download page, Safe Browsing evaluates the page structure, identifies multiple download buttons, and assesses which ones appear legitimate versus deceptive.
If the system detects suspicious download buttons or identifies the page as potentially harmful, modern browsers display prominent warnings. These warnings explain the detected threat, show examples of why the page is considered dangerous, and provide options to proceed with caution or return to safety.
Chrome, Firefox, Safari, and Edge all integrate Safe Browsing technology, though implementations vary. Chrome and Firefox use direct Google Safe Browsing integration, while Safari uses Apple’s similar system informed by Google’s data. Edge uses Microsoft Defender SmartScreen, which incorporates Safe Browsing intelligence alongside Microsoft’s own threat detection.
Enabling Enhanced Safe Browsing
Google Chrome offers Enhanced Safe Browsing, a more aggressive protection mode that provides superior ability to detect fake download buttons and other threats. This feature shares additional browsing data with Google in exchange for faster, more accurate threat detection.
To enable Enhanced Safe Browsing in Chrome, open Settings, navigate to Privacy and security, select Security, and choose “Enhanced protection” under Safe Browsing. This mode checks downloads against Google’s databases more thoroughly and warns about uncommon downloads even if they’re not explicitly flagged as malicious.
Enhanced Safe Browsing also provides real-time URL checking rather than relying solely on cached threat lists. This means protection against newly created phishing pages and malicious downloads that haven’t yet been added to the standard Safe Browsing database.
Understanding Safe Browsing Limitations
While Safe Browsing is powerful, it’s not infallible. New deceptive download pages are created constantly, and there’s always a window between when a malicious page goes live and when Safe Browsing identifies and blocks it. Sophisticated attackers frequently create new domains and pages to stay ahead of detection systems.
Safe Browsing primarily focuses on known malicious content rather than merely deceptive advertising. A page might contain multiple confusing download buttons without technically being “malicious,” meaning Safe Browsing might not flag it even though it’s designed to deceive users.
3. Microsoft Defender SmartScreen Protection
Windows users benefit from Microsoft Defender SmartScreen, an integrated security feature that works across Microsoft Edge and Windows itself to detect fake download buttons and protect against malicious downloads.
SmartScreen’s Multi-Layered Approach
SmartScreen operates at both the browser and operating system levels, providing comprehensive protection throughout the download process. When you click a download button in Edge, SmartScreen first evaluates the source website’s reputation using Microsoft’s global threat intelligence network.
The system analyzes download URLs, file signatures, and behavioral patterns to determine whether a download is legitimate, potentially unwanted, or malicious. This analysis happens in real-time, comparing your download against billions of known files and threat patterns from Microsoft’s cloud intelligence.
SmartScreen maintains reputation scores for both websites and individual files. A file downloaded from a reputable source receives automatic trust, while files from new or suspicious sources trigger warnings or blocks. This reputation system helps SmartScreen distinguish between legitimate software updates and malware disguised as popular applications.
Application Reputation and Download Warnings
When you download a file through Edge, SmartScreen evaluates the file’s digital signature and checks whether it’s commonly downloaded by other users. Uncommon or unsigned files trigger warning dialogs explaining the potential risk.
These warnings display information about why the file is considered potentially dangerous—whether it’s rarely downloaded, from an untrusted publisher, or matches known malware characteristics. Users can choose to keep the file anyway, but the warning ensures informed decision-making.
For files that SmartScreen identifies as definitely malicious, the download is blocked entirely with a red warning screen. These blocks prevent the file from being saved to your computer, protecting you even if you accidentally click a fake download button leading to confirmed malware.
Configuring SmartScreen Settings
SmartScreen is enabled by default in Windows and Microsoft Edge, but you can adjust its settings to match your security preferences. In Edge, navigate to Settings, Privacy, search, and services, and locate the Security section.
Here you’ll find SmartScreen settings including “Block potentially unwanted apps” which specifically targets bundleware and adware commonly associated with fake download buttons. Enabling this option provides additional protection against the unwanted software that legitimate-looking downloads often bundle.
Windows Security settings also control SmartScreen behavior for downloads from all browsers. Open Windows Security from the Start menu, select App & browser control, and review SmartScreen settings for Edge, apps and files, and Microsoft Store apps.
SmartScreen’s Integration with Windows Security
Unlike browser-only protection systems, SmartScreen integrates with Windows Defender Antivirus and the broader Windows Security ecosystem. When you download a file, Windows Security continues monitoring it even after the download completes.
If a downloaded file attempts to execute suspicious behaviors—such as modifying system files, changing browser settings, or installing additional software—Windows Security intervenes with additional warnings or automatic remediation. This multi-stage protection catches threats that evade initial download screening.
4. Firefox’s Enhanced Tracking Protection
Mozilla Firefox includes Enhanced Tracking Protection with specialized features designed to detect fake download buttons by blocking the advertising and tracking scripts that create them.
Blocking Third-Party Scripts and Advertisements
Enhanced Tracking Protection in Firefox automatically blocks many of the third-party advertising scripts responsible for injecting fake download buttons into websites. By preventing these scripts from loading, Firefox eliminates the fake buttons before they ever appear on the page.
This approach differs from systems that identify malicious downloads after you click them. Instead, Firefox prevents the deceptive interface elements from existing in the first place, making it impossible to accidentally click them.
The protection operates in multiple modes—Standard, Strict, and Custom. Standard mode blocks known trackers and third-party cookies while allowing most advertising. Strict mode aggressively blocks almost all trackers and many advertising scripts, significantly reducing fake download button exposure.
Content Blocking and Download Protection
Firefox’s content blocking system identifies and removes page elements that match patterns associated with deceptive advertising. When you visit a download page, Firefox analyzes the page structure and blocks content from known malicious advertising networks.
This blocking happens transparently—you simply see fewer download buttons on the page, with the legitimate button more clearly visible. The eliminated buttons are those sourced from advertising networks with histories of deceptive practices.
To customize content blocking, click the shield icon in Firefox’s address bar when visiting any website. This displays what Firefox has blocked on the current page and allows you to adjust protection levels. You can report problematic sites to help improve Firefox’s ability to detect fake download buttons across the web.
Enabling Maximum Protection in Firefox
For the strongest protection against fake download buttons, configure Firefox with Strict Enhanced Tracking Protection. Open Settings, navigate to Privacy & Security, and select “Strict” under Enhanced Tracking Protection.
Strict mode blocks social media trackers, cross-site cookies, tracking content, cryptominers, and fingerprinting scripts. While this aggressive blocking occasionally causes website functionality issues, it provides maximum protection against deceptive advertising practices.
You can create exceptions for trusted websites that break under strict protection while maintaining strong security for unfamiliar download sites where fake buttons are most common.
Firefox’s Suspicious Site Reporting System
Firefox empowers users to report websites with fake download buttons and other deceptive practices. When you encounter a problematic page, click the shield icon and select “Report a Problem.” This feedback helps Mozilla identify and block deceptive advertising networks.
The reporting system contributes to Firefox’s global protection databases, meaning your report helps protect all Firefox users worldwide. This collaborative approach to security constantly improves Firefox’s ability to identify and block fake download buttons as new deceptive techniques emerge.
5. Safari’s Intelligent Tracking Prevention
Apple’s Safari browser includes Intelligent Tracking Prevention, a privacy-focused system that indirectly helps detect fake download buttons by limiting the tracking and advertising ecosystem that creates them.
Machine Learning-Based Tracker Blocking
Safari uses on-device machine learning to identify tracking scripts and cross-site data collection. While primarily designed for privacy protection, this system also blocks many of the advertising networks that inject fake download buttons into websites.
The machine learning models analyze website behavior patterns to distinguish between essential functionality and tracking/advertising scripts. Known advertising networks are automatically blocked, preventing their deceptive content from loading.
Safari’s approach is privacy-first, meaning it blocks tracking by default without requiring configuration. This automatic protection helps users avoid fake download buttons without needing technical knowledge or manual settings adjustment.
Download Security Warnings
When you download files through Safari, the browser performs security checks using Apple’s threat intelligence. Files from known malicious sources trigger warnings, and Safari automatically quarantines downloaded files for inspection by macOS’s security systems.
The quarantine system adds an extended attribute to downloaded files, signaling to macOS that the file requires additional scrutiny before execution. When you attempt to open a downloaded file, macOS Gatekeeper checks its signature and reputation before allowing it to run.
This multi-layered approach means that even if you click a fake download button and download unwanted software, macOS’s security systems provide additional protection before the software can cause harm.
Fraudulent Website Warnings
Safari includes fraudulent website warnings powered by Google Safe Browsing and Apple’s own threat intelligence. When you navigate to known phishing sites or pages distributing malware, Safari displays full-page warnings explaining the detected threat.
These warnings are particularly relevant for download pages, as many fake download button schemes rely on redirecting users to fraudulent websites that impersonate legitimate software distributors. Safari’s warnings interrupt these redirection chains before downloads begin.
Configuring Safari Security Settings
Safari’s security features are enabled by default, but you can verify and adjust them in Preferences under the Security and Privacy tabs. Ensure “Warn when visiting a fraudulent website” is checked to maintain protection against deceptive download pages.
The Privacy tab contains tracking prevention settings. While you can’t directly adjust Intelligent Tracking Prevention’s behavior, you can enable additional privacy protections like blocking all cookies, which further reduces exposure to advertising-based fake download buttons.
6. Browser Extension Enhancement Options
While built-in browser features provide substantial protection to detect fake download buttons, specialized extensions offer additional layers of security and customization.
uBlock Origin for Advanced Content Filtering
uBlock Origin is a powerful content filtering extension that blocks advertisements, trackers, and malicious scripts. Unlike basic ad blockers, uBlock Origin uses sophisticated filter lists specifically designed to identify and remove fake download buttons.
The extension maintains filter lists curated by security researchers who specifically target deceptive advertising practices. These lists include patterns matching known fake download button implementations, automatically removing them from pages before they render.
Installing uBlock Origin is straightforward—search for it in your browser’s extension store and add it with a single click. After installation, the extension works automatically, though you can access advanced settings to customize filtering behavior and whitelist trusted sites.
Malwarebytes Browser Guard
Malwarebytes Browser Guard specifically targets scam websites, malicious downloads, and deceptive advertising. The extension uses Malwarebytes’ extensive threat intelligence to identify and block websites known for hosting fake download buttons.
When you navigate to a suspicious download page, Browser Guard displays warnings and blocks page elements associated with deceptive practices. The extension also accelerates browsing by blocking resource-intensive advertising scripts.
Browser Guard includes unique features like scam blocking that identifies phishing pages and fraudulent download sites, and clickbait blocking that removes sensationalized advertising often used to disguise fake download buttons.
Bitdefender TrafficLight
Bitdefender TrafficLight provides real-time protection against malicious websites and downloads. The extension checks every link you visit against Bitdefender’s cloud-based threat intelligence, warning you before you reach dangerous pages.
TrafficLight displays security ratings next to search results and social media links, helping you identify safe download sources before clicking. This proactive approach prevents exposure to fake download buttons by steering you away from deceptive websites entirely.
The extension also includes anti-phishing protection and automatically blocks trackers that collect browsing data. This combination of features creates a comprehensive security layer that significantly reduces fake download button exposure.
Balancing Protection with Website Functionality
Aggressive content blocking extensions occasionally interfere with legitimate website functionality. Download buttons—even real ones—sometimes load from content delivery networks or third-party services that extensions might block.
When you encounter a broken download page on a trusted site, temporarily disable your content blocking extensions to determine if they’re causing the issue. You can then create site-specific exceptions that allow the legitimate download while maintaining protection elsewhere.
Most extensions include simple toolbar buttons that let you disable protection for the current site with a single click. Use this feature judiciously, only on websites you trust, to balance security with functionality.
7. Visual Recognition and User Education
Technology alone can’t eliminate the fake download button problem. Understanding how to visually identify and avoid these threats is essential for complete protection.
Visual Characteristics of Fake Download Buttons
Fake download buttons often share distinctive visual characteristics once you know what to look for. They frequently use bright, attention-grabbing colors—especially green, blue, or orange—with bold text and prominent borders designed to attract clicks.
Legitimate download buttons typically match the website’s overall design language and branding. Fake buttons often look generic or use design patterns associated with advertising rather than native website controls. Look for buttons that seem visually inconsistent with the rest of the page.
Many fake buttons include unnecessary urgency messaging, countdowns, or file size information that legitimate software developers rarely display directly on download buttons. These elements create psychological pressure to click quickly without careful evaluation.
URL and Destination Inspection Techniques
Before clicking any download button, hover your mouse cursor over it without clicking. Your browser displays the destination URL in the status bar at the bottom of the window. This simple habit reveals enormous amounts of information about whether a button is legitimate.
Fake download buttons typically link to advertising networks, redirect services, or domains completely unrelated to the software you’re trying to download. Look for URLs containing “ads,” “download,” “get,” or other generic terms combined with unfamiliar domains.
Legitimate download buttons link directly to file downloads from the software publisher’s domain or trusted content delivery networks. A button claiming to download VLC Media Player should link to videolan.org or a recognized CDN, not to an advertising network or redirect service.
Recognizing Page Layout Patterns
Deceptive download pages follow predictable patterns. Multiple prominent download buttons scattered across the page with inconsistent styling indicate probable fake buttons. Legitimate pages typically have a single, clearly marked download button or a small set of clearly differentiated options for different operating systems or versions.
Advertising-heavy pages with minimal actual content often host fake download buttons. If you see more advertising than information about the software you’re downloading, exercise extreme caution with every clickable element.
Pay attention to button positioning. Fake buttons often appear in advertising zones—the top of the page, right sidebar, or within content areas where banner ads typically display. Legitimate download buttons appear in consistent locations within the website’s native layout.
8. Reporting and Community Protection
Individual vigilance helps you avoid fake download buttons, but reporting threats helps protect the entire internet community and improves systems that detect fake download buttons for everyone.
How to Report Malicious Downloads and Sites
Most browsers include built-in reporting mechanisms for fraudulent websites and malicious downloads. In Chrome, click the three-dot menu on warning pages and select “Report details.” This sends information about the threat to Google Safe Browsing for analysis and database updates.
Firefox users can report suspected phishing and malware sites through the Firefox menu under Help, then “Report Deceptive Site.” Edge includes similar reporting options through its security warning pages.
These reports directly improve threat detection systems. When multiple users report the same website, automated systems flag it for additional scrutiny and potentially add it to block lists that protect all users worldwide.
Contributing to Community Protection Databases
Security-focused communities maintain databases of known malicious download sites and fake button implementations. Contributing to these databases helps protect others while improving the collective ability to detect fake download buttons.
Websites like URLhaus by Abuse.ch allow users to submit malicious URLs for community verification and blocking. PhishTank enables crowdsourced phishing site identification. Contributing to these databases takes minutes but provides lasting protection for internet users globally.
Browser extension developers also accept threat submissions through their respective communities and support channels. If you encounter a fake download button that bypasses existing filters, report it to extension developers so they can update their filter lists.
Educating Others About Download Safety
Personal knowledge about fake download buttons becomes exponentially more valuable when shared. Many internet users—particularly less technical individuals and elderly users—lack awareness of these threats and regularly fall victim to deceptive downloads.
Take time to educate family members, friends, and colleagues about fake download button risks. Show them how to identify suspicious buttons, demonstrate browser security features, and explain the importance of hovering over links before clicking.
Creating awareness in your community reduces the financial incentives for websites to host fake download buttons. As more users learn to avoid these threats, the advertising revenue they generate declines, gradually reducing their prevalence across the web.
9. Advanced Technical Protections
For technically proficient users, additional measures can supplement browser features that detect fake download buttons with system-level protections.
Hosts File and DNS-Level Blocking
Advanced users can implement network-level blocking that prevents connections to known malicious advertising networks. The hosts file—a system file that maps domain names to IP addresses—can be configured to redirect advertising domains to localhost, preventing fake download button scripts from loading.
Projects like StevenBlack’s hosts file compilations provide regularly updated lists of advertising and malware domains. Downloading and implementing these hosts files blocks thousands of known threat sources at the operating system level, protecting all browsers and applications simultaneously.
DNS-level filtering services like Pi-hole, NextDNS, or AdGuard DNS provide similar protection without requiring hosts file management. These services filter DNS requests, preventing resolution of known malicious domains before your browser even attempts to connect.
Virtual Machine Isolation for Untrusted Downloads
When you must download files from questionable sources, using virtual machines provides complete isolation from your main operating system. Software like VirtualBox or VMware allows you to create disposable virtual environments where suspicious downloads can be tested safely.
Download and open files within the virtual machine. If they contain malware or unwanted software, the infection remains contained within the virtual environment and can’t affect your actual computer. Simply delete the virtual machine and create a fresh one for future risky downloads.
This approach is particularly valuable for software development, malware research, or situations where you must interact with download sources of uncertain trustworthiness.
Sandboxing Applications
Windows Sandbox and similar sandboxing technologies create isolated environments for running untrusted applications. Unlike virtual machines, sandboxes are lightweight and integrate closely with your main operating system while maintaining security boundaries.
Enable Windows Sandbox through Windows Features on Professional and Enterprise editions of Windows. When you download a suspicious file, right-click it and select “Run in Windows Sandbox.” The file executes in an isolated environment where it can’t access your actual files or modify system settings.
Any changes made within the sandbox disappear when you close the sandbox window, providing temporary execution environments perfect for testing suspicious downloads.
Script Blocking and NoScript Extensions
Extensions like NoScript for Firefox or ScriptSafe for Chrome block all JavaScript execution by default, allowing it only on trusted websites. Since fake download buttons rely heavily on JavaScript for their deceptive behaviors, blocking scripts eliminates most threats automatically.
This aggressive approach breaks many legitimate websites, requiring you to manually whitelist sites and specific script sources. However, for users comfortable with this tradeoff, script blocking provides extremely strong protection against fake download buttons and numerous other web-based threats.
10. Mobile Device Protection Strategies
Smartphones and tablets face unique challenges regarding fake download buttons, but mobile browsers include specialized protections to detect fake download buttons on smaller screens.
Mobile Browser Security Features
Chrome, Safari, and Firefox on mobile devices include the same Safe Browsing and security features as their desktop counterparts. However, mobile implementations sometimes differ due to screen size constraints and touch input considerations.
Mobile browsers often display more prominent security warnings since the reduced screen space makes it harder to verify URLs and inspect page elements. Full-screen warnings with clear options to proceed or go back help mobile users make informed decisions about suspicious downloads.
Google Play Protect on Android and iOS’s App Store review processes provide additional protection layers. These systems scan apps before allowing installation, catching malware that might have been downloaded through fake download buttons.
Avoiding Third-Party App Stores
Mobile devices are particularly vulnerable when users install apps from sources outside official app stores. Fake download buttons frequently promote unofficial app stores or direct APK downloads that bypass Google Play Protect and other security measures.
Only download mobile apps from official sources—Google Play Store for Android or Apple App Store for iOS. These platforms vet applications and provide security scanning that identifies malware before it reaches your device.
If you must install apps from alternate sources on Android, ensure Google Play Protect is enabled and carefully review all permission requests during installation. Any app requesting excessive permissions relative to its stated functionality should be considered suspicious.
Mobile Ad Blocking Solutions
Mobile browsing often exposes users to more aggressive advertising, including fake download buttons in pop-ups and redirects. Mobile ad blockers provide protection by preventing these advertising elements from loading.
Firefox for Android supports desktop extensions including uBlock Origin, providing comprehensive ad and tracker blocking on mobile devices. Chrome for Android doesn’t support extensions, but Brave Browser includes built-in ad blocking with strong protection against deceptive advertising.
iOS users can enable content blockers through Safari’s settings. Popular options like 1Blocker, AdGuard, and Wipr block advertising and tracking scripts that create fake download buttons, significantly improving mobile browsing safety.
11. Enterprise and Educational Environment Protection
Organizations face unique challenges protecting users from fake download buttons, but enterprise-grade browser management provides powerful tools to detect fake download buttons across entire networks.
Group Policy and Browser Management
Enterprise environments can enforce browser security settings through Group Policy on Windows or mobile device management solutions. Administrators can mandate Safe Browsing, SmartScreen, or equivalent protections across all organizational devices.
These centrally managed policies prevent users from disabling security features, ensuring consistent protection regardless of individual user preferences or technical knowledge. Administrators can also block specific websites known for hosting fake download buttons.
Browser management platforms like Chrome Enterprise allow administrators to deploy extensions automatically, configure content filtering, and monitor security events across the organization. This centralized approach provides visibility into threats that individual users encounter.
Network-Level Content Filtering
Enterprise firewalls and web filters can block known malicious advertising networks at the network perimeter. Products like Cisco Umbrella, Palo Alto Networks, or Fortinet provide cloud-based filtering that inspects all web traffic for threats before it reaches end-user devices.
These systems maintain massive threat intelligence databases specifically targeting malware distribution, phishing, and deceptive advertising. Network-level blocking provides protection even for unmanaged personal devices that connect to the organization’s network.
User Education and Security Awareness Training
Technical controls alone can’t eliminate fake download button risks in organizational environments. Regular security awareness training teaches employees to recognize and avoid these threats independently.
Training programs should include practical examples of fake download buttons, hands-on exercises identifying deceptive elements, and clear reporting procedures when employees encounter suspicious download pages. Regular reinforcement through phishing simulations and security newsletters keeps awareness high.
Organizations should foster cultures where reporting suspicious downloads is encouraged and easy, creating feedback loops that help IT teams identify new threats and adjust protections accordingly.
12. Future Developments in Download Button Detection
The ongoing arms race between security professionals and malicious actors continues evolving. Understanding future directions helps anticipate how browsers will detect fake download buttons in coming years.
AI and Machine Learning Advancements
Future browser security will increasingly rely on artificial intelligence and machine learning models capable of identifying deceptive user interface patterns in real-time. These models can analyze visual elements, layout patterns, and behavioral characteristics to distinguish legitimate downloads from fakes with superhuman accuracy.
Training data from billions of flagged pages allows machine learning systems to recognize subtle patterns humans might miss. As these models improve, they’ll provide instant protection against even novel fake button techniques never seen before.
Browser vendors are investing heavily in this technology. Google’s AI research directly feeds into Safe Browsing improvements, while Microsoft leverages machine learning across its Defender security ecosystem. These investments promise increasingly effective automatic detection systems.
Standardized Download Button Patterns
Web standards organizations are exploring standardized patterns for download buttons that browsers can identify and preferentially highlight. Just as browsers can identify and autofill form fields, they might someday recognize legitimate download buttons and visually emphasize them while dimming suspicious alternatives.
This approach would provide visual cues helping users identify real download buttons at a glance. Standards-compliant download buttons would receive visual treatment signaling their legitimacy, while non-standard implementations would appear less prominent.
Blockchain-Based Reputation Systems
Decentralized reputation systems using blockchain technology could provide tamper-proof records of website and download trustworthiness. Users could contribute reputation data about their download experiences, creating community-verified authenticity scores for downloads and websites.
These systems would resist manipulation by malicious actors while providing transparent, verifiable reputation information. Browsers could display reputation scores derived from decentralized data, helping users make informed decisions about which download buttons to trust.
Conclusion: Taking Control of Your Download Security
The proliferation of fake download buttons across the internet represents one of the most persistent security challenges facing casual users today. However, modern browsers include sophisticated features specifically designed to detect fake download buttons and protect you from their harmful consequences.
By enabling and understanding built-in security features like Google Safe Browsing, Microsoft Defender SmartScreen, Firefox Enhanced Tracking Protection, and Safari’s Intelligent Tracking Prevention, you create multiple layers of defense against deceptive downloads. These systems work automatically in the background, warning you about threats before you can accidentally click them.
Supplementing browser protections with carefully chosen security extensions provides additional filtering and threat detection. Extensions like uBlock Origin, Malwarebytes Browser Guard, and Bitdefender TrafficLight offer specialized capabilities that complement and enhance your browser’s native security features.
Perhaps most importantly, developing visual recognition skills and cautious browsing habits transforms you from a passive victim into an active defender of your own security. Learning to identify suspicious button characteristics, inspecting URLs before clicking, and recognizing common deceptive page layouts provides protection that no automated system can fully replace.
The ability to confidently download legitimate software without fear of accidentally clicking fake buttons is within reach. Enable your browser’s security features today, consider adding reputable security extensions, and take a few moments to educate yourself about visual warning signs. These simple steps provide comprehensive protection that allows you to navigate download pages with confidence.
Also read this:
Recover Deleted Photos Without Apps Using This Phone Setting: The Complete Recovery Guide
This Browser Setting Instantly Speeds Up Slow Websites: The Ultimate Guide