hidden Android setting protects Public Wi-Fi networks are everywhere—coffee shops, airports, hotels, restaurants, and shopping malls all offer free internet access to attract customers and provide convenience. While connecting to these networks seems harmless, it exposes your device to serious security risks that most people never consider. Hackers specifically target public Wi-Fi because users often let their guard down, creating perfect opportunities for data theft, account hijacking, and malware distribution.
What many Android users don’t realize is that their device already contains powerful protection against these threats. Buried deep within your phone’s settings is a hidden Android setting that protects you from the most common and dangerous public Wi-Fi attacks. This feature doesn’t require expensive security subscriptions or complicated technical knowledge—it’s built right into your operating system, waiting to be activated.
This comprehensive guide will reveal exactly what this hidden Android setting protects against, how to enable it properly, and why every smartphone user should activate it immediately. You’ll learn about the specific vulnerabilities of public networks, the sophisticated attacks hackers use, and the simple steps to secure yourself completely. By the end of this article, you’ll have transformed your Android phone into a fortress against Wi-Fi-based threats.
1. Understanding Public Wi-Fi Security Risks
The Hidden Dangers of Free Internet
Public Wi-Fi networks create an inherently insecure environment where multiple unknown users share the same connection. This hidden Android setting protects against vulnerabilities that exist by design in these networks:
Network Architecture Vulnerabilities
- Open networks with no password requirements
- Shared network space with strangers and potential attackers
- Minimal or non-existent encryption between devices
- Easy interception of data transmitted over the network
- No verification of network legitimacy or operator identity
- Outdated router firmware with known security flaws
User Behavior Factors
- False sense of security in commercial establishments
- Automatic connection to familiar network names
- Assumption that business networks are professionally secured
- Checking sensitive accounts while on public Wi-Fi
- Ignoring security warnings about network safety
- Using same passwords across multiple accounts
Common Attack Vectors Explained
Understanding what this hidden Android setting protects against requires knowing how attackers exploit public Wi-Fi:
Man-in-the-Middle Attacks
- Attacker positions themselves between your device and the internet
- All data passes through their system before reaching destination
- Ability to read, modify, or inject content into your traffic
- Capture of login credentials, credit card numbers, and personal information
- Session hijacking allows takeover of active accounts
- Often completely invisible to the victim
Evil Twin Networks
- Fake Wi-Fi hotspots with names similar to legitimate ones
- “Starbucks_WiFi” vs. “Starbucks-WiFi” or “StarbucksGuest”
- Stronger signal than legitimate network attracts connections
- Complete control over all traffic passing through fake network
- Installation of malware and credential harvesting
- Victims believe they’re using official network
Packet Sniffing
- Capturing all data transmitted across the network
- Specialized software analyzes packets for valuable information
- Extraction of unencrypted passwords and personal data
- Building profiles of user behavior and interests
- Long-term surveillance of target individuals
- Legal in some jurisdictions for network operators
DNS Spoofing
- Redirecting your web requests to malicious servers
- Fake banking or shopping websites that look legitimate
- Credential theft through convincing phishing pages
- Malware distribution through fake software updates
- Complete subversion of your browsing experience
- Difficult to detect without careful examination
Session Hijacking
- Stealing active session cookies and tokens
- Taking over logged-in accounts without passwords
- Access to email, social media, and banking accounts
- Ability to perform actions as the legitimate user
- Often combined with other attack techniques
- Can persist even after leaving the network
Real-World Attack Statistics
The numbers reveal why this hidden Android setting protects is so critical:
- Over 40% of users have experienced data compromise on public Wi-Fi
- Hackers can intercept unencrypted traffic in under 10 minutes
- 70% of public Wi-Fi hotspots have inadequate security measures
- Financial losses from public Wi-Fi attacks exceed 400 million dollars annually
- Average time to detect a public Wi-Fi breach is 6-8 months
- 90% of public Wi-Fi users access sensitive accounts regularly
- Only 1 in 4 users employs any protection on public networks
2. Revealing Android’s Hidden Wi-Fi Protection
What Is the Hidden Security Feature?
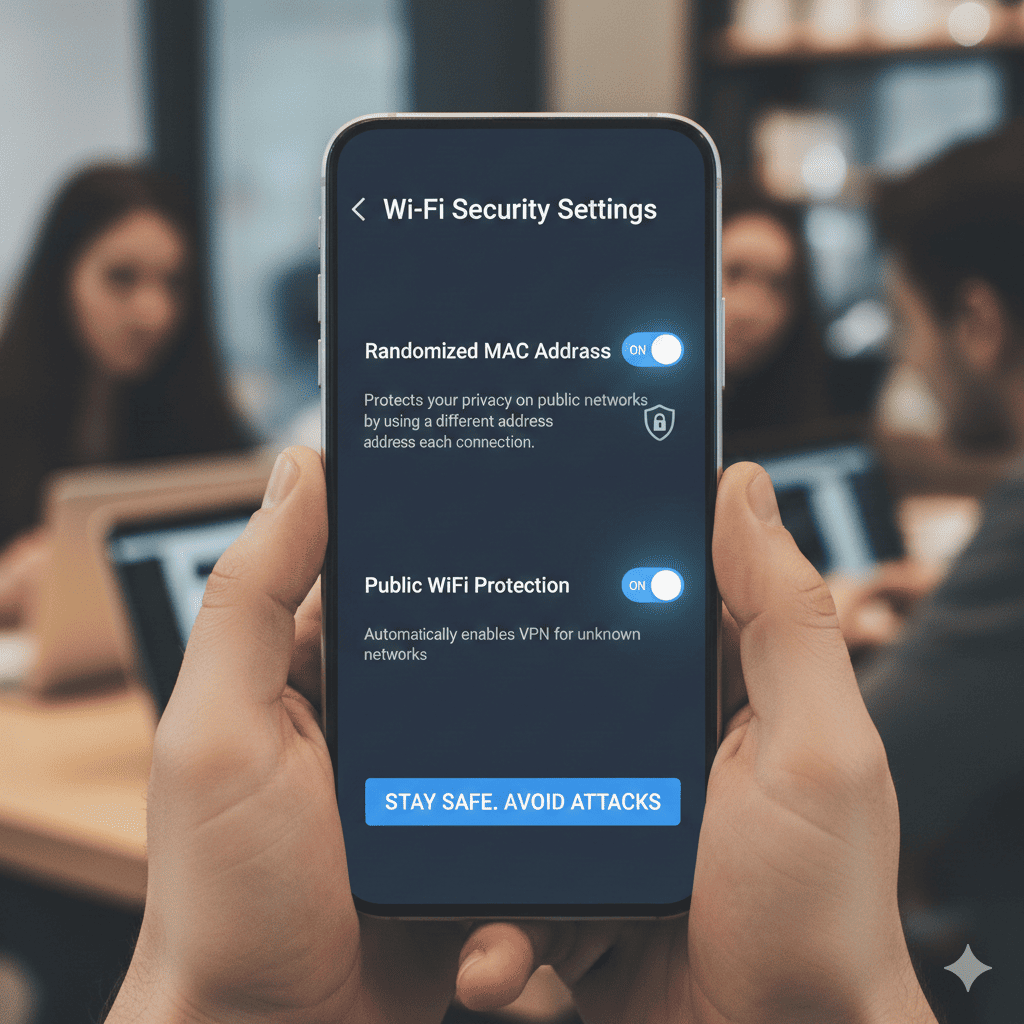
The powerful capability that many don’t know exists is Android’s combination of MAC Address Randomization and Private DNS. This hidden Android setting protects your identity and traffic through multiple sophisticated mechanisms that work together to create a secure connection even on dangerous networks.
MAC Address Randomization
- Changes your device’s unique hardware identifier for each network
- Prevents tracking across different locations and times
- Makes it impossible to build movement profiles
- Stops targeted attacks based on known device signatures
- Creates new identity for each connection session
- Works automatically once enabled
Private DNS (DNS over TLS)
- Encrypts DNS queries preventing interception and manipulation
- Verifies authenticity of DNS responses
- Protects against DNS spoofing and hijacking
- Ensures you reach legitimate websites
- Works on any network including public Wi-Fi
- Maintained by trusted DNS providers
Always-On VPN
- Built-in VPN configuration that blocks internet without VPN connection
- Ensures all traffic is encrypted before leaving device
- Prevents accidental exposure on public networks
- Works with third-party VPN applications
- Blocks connections if VPN drops
- Provides comprehensive protection layer
How These Technologies Work Together
Understanding how this hidden Android setting protects you requires examining the layered approach:
First Layer: Identity Protection
- MAC randomization prevents device fingerprinting
- Each network sees a different device identifier
- Tracking across locations becomes impossible
- Your movement patterns remain private
- Targeted attacks against specific devices fail
Second Layer: DNS Security
- All DNS queries encrypted and authenticated
- Attackers cannot redirect you to fake sites
- DNS poisoning attacks rendered ineffective
- Your browsing destinations remain private
- Malicious DNS servers cannot affect you
Third Layer: Traffic Encryption
- VPN encrypts all data before transmission
- Man-in-the-middle attacks see only encrypted data
- Even network operator cannot read your traffic
- Session hijacking becomes impossible
- Complete protection of all applications
Why Most Users Never Enable This Protection
Despite how effectively this hidden Android setting protects users, it remains largely unknown:
Discovery Challenges
- Features scattered across different settings menus
- Technical terminology confuses average users
- No prominent setup wizard during phone initialization
- Manufacturers don’t highlight these features in marketing
- Settings buried under advanced or developer options
- Lack of user education about public Wi-Fi risks
Perceived Complexity
- Users assume VPNs require paid subscriptions
- Technical settings appear intimidating
- Fear of breaking existing functionality
- Uncertainty about proper configuration
- Assumption that default settings are sufficient
Performance Concerns
- Misconception that security features slow down connection
- Battery life concerns about continuous encryption
- Data usage worries with VPN connections
- Compatibility fears with certain applications
- Preference for convenience over security
3. Complete Step-by-Step Activation Guide
Enabling MAC Address Randomization
First component of how this hidden Android setting protects your device:
For Android 10 and Later:
- Open Settings application
- Navigate to Network & Internet or Connections
- Tap on Wi-Fi settings
- Select Wi-Fi preferences or Advanced
- Find “Use randomized MAC” option
- Enable toggle for randomized MAC addresses
- Choose “Use randomized MAC” for all networks
- Confirm the setting is active
Per-Network Configuration:
- Go to Wi-Fi settings
- Long-press on connected or saved network
- Select “Modify network” or network details
- Expand Advanced options
- Locate Privacy or MAC address setting
- Change from “Phone MAC” to “Randomized MAC”
- Save the modified network configuration
- Repeat for all saved networks
Samsung Devices:
- Open Settings menu
- Select Connections
- Tap Wi-Fi
- Tap three-dot menu icon
- Choose Advanced
- Enable “Use randomized MAC”
- Apply to all networks or configure individually
Configuring Private DNS
Second critical component where this hidden Android setting protects against attacks:
Setting Up Private DNS:
- Navigate to Settings
- Select Network & Internet or Connections
- Tap on Advanced or More connection settings
- Choose Private DNS
- Select “Private DNS provider hostname”
- Enter one of these trusted providers:
- dns.google
- cloudflare-dns.com
- dns.quad9.net
- Tap Save or Apply
- Verify connection with status message
Recommended DNS Providers:
Google Public DNS
- Hostname: dns.google
- Fast performance and global infrastructure
- Strong privacy policy and transparency
- Excellent reliability and uptime
- Free to use for everyone
Cloudflare DNS
- Hostname: cloudflare-dns.com
- Focus on privacy with no logging
- Fast response times worldwide
- Regular transparency reports published
- Committed to user privacy
Quad9 DNS
- Hostname: dns.quad9.net
- Security focus with malware blocking
- Non-profit organization operation
- Privacy-respecting service
- Threat intelligence integration
Setting Up Always-On VPN
The final layer where this hidden Android setting protects comprehensively:
Built-In VPN Configuration:
- First, install your preferred VPN application
- Open Settings on your device
- Go to Network & Internet
- Select VPN settings
- Add VPN configuration or choose installed VPN
- Tap the gear icon next to VPN connection
- Enable “Always-on VPN” toggle
- Enable “Block connections without VPN”
- Save configuration changes
- Test by disabling VPN temporarily
Recommended VPN Providers:
For Maximum Security
- ProtonVPN: Strong privacy focus, Swiss jurisdiction
- Mullvad: Anonymous accounts, no logging
- IVPN: Transparent operation, privacy audits
For Balance of Features
- NordVPN: Large server network, good speeds
- ExpressVPN: User-friendly, reliable performance
- Surfshark: Unlimited devices, affordable pricing
Free Options
- ProtonVPN Free: Limited servers but no data cap
- Windscribe: 10GB monthly free data
- Hide.me: 10GB monthly with good privacy policy
Verifying Your Protection
Confirm that this hidden Android setting protects you properly:
MAC Randomization Check:
- Connect to Wi-Fi network
- Check Wi-Fi details in settings
- Verify MAC address shown is randomized
- Disconnect and reconnect to see new MAC
- Confirm different from physical MAC address
Private DNS Verification:
- Visit dns.google/query
- Confirm you’re using encrypted DNS
- Check for TLS indicator in results
- Test DNS leak on dnsleaktest.com
- Verify no information leakage
VPN Protection Test:
- Visit ipleak.net with VPN connected
- Confirm your real IP is hidden
- Check for DNS leaks showing your ISP
- Verify WebRTC doesn’t reveal real IP
- Disable VPN and confirm internet blocks
4. Understanding Protection Layers in Detail
MAC Address Randomization Deep Dive
How this aspect of the hidden Android setting protects your privacy:
What Is a MAC Address?
- Media Access Control address is unique device identifier
- Assigned by manufacturer to network hardware
- Remains constant across all connections
- Used by networks to identify and track devices
- Traditionally unchangeable and permanent
- First half identifies manufacturer, second half is unique number
Privacy Implications of Static MAC
- Retailers track shopping behavior across visits
- Advertisers build profiles of location patterns
- Networks correlate devices with specific individuals
- Movement between locations can be mapped
- Historical connection data reveals routines
- Cross-network tracking enables surveillance
How Randomization Protects You
- New MAC address generated for each network
- Previous connection history cannot be linked
- Tracking across locations becomes impossible
- Each connection appears as different device
- Privacy maintained in public spaces
- Control over your digital footprint
Technical Implementation
- Android generates locally administered MAC
- Maintains randomization per network SSID
- Consistent MAC per network for functionality
- Changes when forgetting and reconnecting
- Hardware MAC never transmitted
- Seamless operation with network requirements
Private DNS Security Benefits
How encrypted DNS within this hidden Android setting protects against manipulation:
Traditional DNS Vulnerabilities
- Queries sent in plain text across network
- Anyone can read your browsing destinations
- Easy to intercept and modify responses
- Attacker can redirect to malicious sites
- ISP and network operators see all DNS queries
- Building detailed profile of online activity
DNS over TLS Protection
- Encryption prevents query interception
- Authentication ensures response legitimacy
- Man-in-the-middle attacks defeated
- Your browsing remains private
- Trusted resolver prevents poisoning
- End-to-end security for DNS traffic
Additional Benefits
- Protection from ISP DNS manipulation
- Access to censored or geo-blocked content
- Faster resolution with quality providers
- Malware blocking with security-focused DNS
- Parental controls with family-safe options
- Consistent experience across all networks
VPN Encryption Comprehensive Coverage
The strongest component where this hidden Android setting protects all traffic:
What VPN Encryption Provides
- All internet traffic encrypted before transmission
- Network operators see only encrypted tunnel
- Destination servers see VPN provider IP
- Complete protection of all applications
- Secure even on completely compromised networks
- Military-grade encryption standards
Types of Traffic Protected
- Web browsing and HTTPS connections
- Email sending and receiving
- Instant messaging and video calls
- File uploads and downloads
- App data synchronization
- Background updates and notifications
Always-On VPN Advantages
- No possibility of accidental unprotected connections
- Protection starts before you remember to activate
- Eliminates human error factor
- Continuous monitoring and reconnection
- Peace of mind on any network
- Comprehensive security posture
5. Optimizing Performance and Compatibility
Balancing Security with Usability
Ensuring this hidden Android setting protects without causing problems:
Network Compatibility Considerations
- Some captive portals require disabling randomization temporarily
- Hotel networks may need device registration
- Corporate networks might require specific MAC addresses
- Public transportation Wi-Fi may have restrictions
- Educational institution networks often have policies
- Guest networks might not support randomized MAC
Managing Network-Specific Settings
- Configure randomization per-network basis
- Disable only for trusted networks requiring it
- Re-enable immediately after leaving restricted network
- Document networks where modifications needed
- Regular review of network-specific configurations
- Balance convenience with security requirements
Battery and Data Optimization
Minimizing impact while maintaining how this hidden Android setting protects:
Battery Consumption Management
- Modern VPNs optimized for mobile devices
- Minimal additional battery drain (2-5%)
- Choose lightweight VPN protocols like WireGuard
- Configure VPN to pause during idle periods
- Disable VPN on trusted home networks
- Monitor battery usage in settings
Data Usage Considerations
- VPN adds 10-20% overhead to data consumption
- Encryption increases packet sizes slightly
- Choose VPN with data compression features
- Monitor usage with built-in Android tools
- Use Wi-Fi whenever possible to preserve mobile data
- Configure apps to limit background data on VPN
Troubleshooting Common Issues
When this hidden Android setting protects too aggressively or causes problems:
Connection Problems
- Some networks reject randomized MAC addresses
- Switch to device MAC temporarily for connection
- Contact network administrator about randomization support
- Use different VPN server if current one is blocked
- Clear Wi-Fi saved networks and reconfigure
- Update VPN application to latest version
Speed and Performance
- Choose geographically closer VPN servers
- Use faster VPN protocols (WireGuard over OpenVPN)
- Test different DNS providers for better performance
- Disable VPN split tunneling if causing issues
- Check for ISP throttling of VPN traffic
- Upgrade VPN plan for higher speed tiers
Compatibility Issues
- Some apps detect and block VPN usage
- Banking apps may require VPN exclusion
- Streaming services might restrict VPN access
- Use VPN split tunneling for specific apps
- Configure per-app VPN rules in Android
- Contact app developers about VPN compatibility
6. Advanced Security Configurations
Network Trust Profiles
Customizing how this hidden Android setting protects based on network type:
Trusted Home Network
- Disable VPN to maximize speed
- Keep Private DNS enabled
- Use device MAC for router optimization
- Allow direct connections for smart home devices
- Configure port forwarding if needed
- Regular router security updates
Work Network Configuration
- Follow company security policies
- May require specific VPN or no VPN
- Coordinate with IT department
- Use company-provided DNS if required
- Comply with device management policies
- Separate work profile for isolation
Public Network Maximum Security
- Always enable VPN before connecting
- Use randomized MAC addresses
- Private DNS with security-focused provider
- Disable file sharing and network discovery
- Turn off automatic connection to open networks
- Monitor for evil twin networks
Enhanced Privacy Measures
Going beyond basic ways this hidden Android setting protects:
Additional Android Privacy Settings
- Disable Wi-Fi scanning when Wi-Fi is off
- Turn off Bluetooth scanning for location
- Restrict app location access to “Only while using”
- Disable usage and diagnostics data collection
- Review and revoke unnecessary app permissions
- Enable Google Play Protect for app scanning
Browser Security Configuration
- Use privacy-focused browsers like Firefox or Brave
- Enable HTTPS-only mode for all connections
- Install HTTPS Everywhere extension
- Block third-party cookies and trackers
- Use DuckDuckGo or Startpage for searches
- Clear cookies and cache regularly
Application Security
- Enable two-factor authentication on all accounts
- Use password manager for unique passwords
- Avoid sensitive transactions on public Wi-Fi even with protection
- Keep all apps updated to latest versions
- Uninstall unused applications
- Review app permissions quarterly
Multi-Device Protection Strategy
Extending how this hidden Android setting protects across devices:
Securing All Your Devices
- Apply same configurations to tablets
- Protect family members’ devices
- Use family VPN accounts with multiple connections
- Share network safety knowledge
- Create household security standards
- Regular security check-ins
Cross-Platform Considerations
- iOS devices have similar privacy features
- Windows and Mac laptops need VPN protection
- Smart home devices should be isolated
- Gaming consoles require special configuration
- Configure router-level VPN for all devices
- Consistent security posture everywhere
7. Recognizing and Avoiding Wi-Fi Threats
Identifying Suspicious Networks
Even with how this hidden Android setting protects you, awareness helps:
Red Flags for Fake Networks
- Networks with slightly misspelled business names
- Multiple networks with similar names
- Unusually strong signals in unexpected places
- No password requirement in sensitive locations
- Requests for personal information to connect
- Immediate redirects after connecting
Verification Techniques
- Ask staff for official network name
- Check for posted Wi-Fi information
- Look for network operated by known provider
- Verify SSID matches exactly
- Confirm network appears on official app
- Trust your instincts about suspicious networks
Safe Public Wi-Fi Practices
Behaviors that complement how this hidden Android setting protects:
Pre-Connection Precautions
- Enable VPN before accessing public Wi-Fi
- Verify network legitimacy with staff
- Forget network after use
- Disable automatic reconnection to open networks
- Check device security settings before connecting
- Have mobile data as backup option
While Connected Practices
- Avoid logging into sensitive accounts
- Never enter credit card information
- Don’t access banking or financial applications
- Keep sessions short and purposeful
- Monitor for unusual behavior or popups
- Use HTTPS websites exclusively
Post-Connection Security
- Forget network from saved networks list
- Clear browser cache and cookies
- Log out of all accounts accessed
- Change passwords if any sensitive activity occurred
- Monitor accounts for suspicious activity
- Run security scan on device
Incident Response Procedures
If you suspect this hidden Android setting protects may have failed:
Immediate Actions
- Disconnect from network immediately
- Disable Wi-Fi completely
- Switch to mobile data connection
- Run antivirus and security scans
- Change passwords for all accounts accessed
- Enable alerts for account access
Follow-Up Measures
- Contact financial institutions about potential compromise
- Monitor credit reports for suspicious activity
- Enable fraud alerts with credit bureaus
- Document timeline and networks used
- Report suspicious networks to authorities
- Review account activity for several months
8. Understanding Legal and Ethical Aspects
Privacy Laws and Public Wi-Fi
How regulations support what this hidden Android setting protects:
Data Protection Regulations
- GDPR requires consent for tracking in Europe
- CCPA provides California consumer privacy rights
- ePrivacy Directive regulates electronic communications
- Local laws vary by jurisdiction
- MAC randomization helps comply with privacy laws
- Your right to privacy on public networks
Network Operator Responsibilities
- Duty to secure public Wi-Fi infrastructure
- Requirements to warn users of risks
- Liability for inadequate security measures
- Obligation to prevent illegal activities
- Transparency about data collection
- Compliance with telecommunications regulations
Ethical Use of Protection Features
Responsible use of how this hidden Android setting protects:
Legitimate Use Cases
- Protecting personal privacy and data
- Preventing identity theft and fraud
- Securing business communications
- Protecting vulnerable family members
- Maintaining digital rights and freedoms
- Avoiding unwanted tracking and profiling
Inappropriate Uses to Avoid
- Evading legitimate network restrictions
- Conducting illegal activities under VPN cover
- Circumventing geographic content restrictions commercially
- Violating terms of service agreements
- Attacking or testing others’ networks without permission
- Using protection to harass or harm others
9. Future of Mobile Wi-Fi Security
Emerging Standards and Technologies
Evolution of how this hidden Android setting protects will advance:
Wi-Fi 6 and 7 Security Improvements
- WPA3 encryption as standard requirement
- Enhanced open network protection
- Individualized data encryption on public networks
- Stronger password protections
- Forward secrecy preventing historical decryption
- Improved protection against offline attacks
Advanced Authentication Methods
- Passpoint for automatic secure connection
- Certificate-based authentication
- Biometric network access
- Zero-trust networking models
- Continuous authentication during sessions
- AI-powered threat detection
Next-Generation VPN Technologies
- Quantum-resistant encryption algorithms
- Decentralized VPN networks
- Built-in operating system VPN
- Zero-configuration automatic protection
- Seamless global server switching
- Enhanced privacy with no-log guarantees
Android Security Roadmap
Google’s plans for enhancing what this hidden Android setting protects:
Short-Term Improvements
- More prominent security warnings
- Simplified privacy feature activation
- Better user education about risks
- Enhanced automatic protection
- Integration with Google One VPN
- Improved compatibility with all networks
Long-Term Vision
- Complete automatic security configuration
- AI-driven threat detection and response
- Seamless protection requiring no user action
- Universal strong encryption
- Elimination of public Wi-Fi vulnerabilities
- Privacy-first design in all features
Industry Collaboration
How various entities work together to enhance what this hidden Android setting protects:
Public-Private Partnerships
- Secure public Wi-Fi infrastructure standards
- Government certification programs
- Industry best practices development
- Shared threat intelligence
- Consumer education initiatives
- Research and development funding
Global Coordination
- International cybersecurity standards
- Cross-border data protection agreements
- Harmonized privacy regulations
- Cooperative law enforcement
- Academic research collaboration
- Open-source security tools
10. Taking Action and Staying Protected
Implementation Action Plan
Immediate steps to activate how this hidden Android setting protects you:
Today’s Tasks (15 minutes)
- Enable MAC address randomization
- Configure Private DNS with trusted provider
- Install and configure VPN application
- Enable Always-on VPN with block without VPN
- Test all settings for proper operation
- Bookmark this guide for reference
This Week’s Tasks
- Configure family members’ devices
- Document your security settings
- Test protection on various networks
- Set up automatic VPN payments
- Create password manager account
- Enable two-factor authentication everywhere
Monthly Maintenance
- Review and update security settings
- Check for Android security updates
- Verify VPN subscription is active
- Test DNS and VPN protection
- Review saved Wi-Fi networks and remove unused
- Audit app permissions and revoke unnecessary access
Building Security Awareness
Spreading knowledge about how this hidden Android setting protects:
Personal Network
- Share this guide with family and friends
- Help elderly relatives configure protection
- Discuss public Wi-Fi risks openly
- Lead by example in security practices
- Offer assistance with technical setup
- Create family security standards
Community Impact
- Write about security on social media
- Present at community organizations
- Volunteer to help vulnerable populations
- Advocate for better public Wi-Fi security
- Support privacy-focused organizations
- Participate in security awareness campaigns
Resources for Continued Learning
Staying informed as threats evolve and this hidden Android setting protects improves:
Educational Resources
- Android Security Blog for official updates
- Electronic Frontier Foundation for privacy news
- Krebs on Security for threat intelligence
- r/Android and r/privacy communities
- NIST Cybersecurity Framework guidelines
- SANS Internet Storm Center
Testing and Validation Tools
- dnsleaktest.com for DNS verification
- ipleak.net for comprehensive leak testing
- Wireshark for network traffic analysis
- Network analyzer apps for monitoring
- Security audit tools and scanners
- VPN speed testing services
Conclusion: Your Security Is in Your Hands
The revelation that this hidden Android setting protects you from public Wi-Fi attacks should be both empowering and motivating. Your device already contains sophisticated security technology that rivals expensive enterprise solutions—it simply needs to be activated. There’s no reason to remain vulnerable when comprehensive protection is literally a few taps away in your settings menu.
Public Wi-Fi will continue to be an essential part of modern life, providing connectivity in countless situations where mobile data is unavailable or impractical. However, convenience should never come at the cost of security. By enabling MAC address randomization, Private DNS, and Always-on VPN, you create multiple layers of defense that protect against virtually all common public Wi-Fi attacks. This hidden Android setting protects not just your data, but your financial security, personal privacy, and digital identity.
The threats are real and constantly evolving. Hackers target public networks because they offer easy access to large numbers of potential victims who often have their guard down. But with proper configuration, you can use public Wi-Fi with confidence, knowing that your device is actively protecting you from these threats. The encryption, anonymization, and authentication provided by these features transform dangerous networks into reasonably safe connections.
Don’t delay implementing these protections. The next public Wi-Fi network you connect to could be compromised, operated by criminals, or monitored by those with malicious intent. Take 15 minutes right now to follow the activation steps in this guide. Enable all three protection layers, test them thoroughly, and then help others do the same. Your future self—and potentially your bank account—will thank you for taking this critical security step today. The hidden Android setting protects effectively, but only if you activate it.
Also read this:
Android Phones Can Lock Themselves Automatically When You Walk Away
This Android Feature Silently Blocks Scam Calls Without Any App
This Built-In Android Feature Warns You While Walking — Most Users Don’t Know